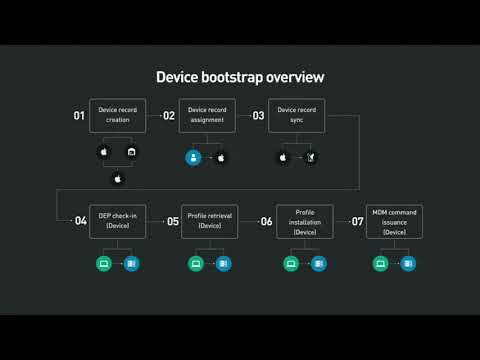
True", everyone! Welcome to our session on a deep dive into macOS MDM. My name is Jesse Endel, and I'm Max Vanilla J. I work at a company called Fleet Smith, which is an Apple device management product, and I'm a staff engineer. Let me give you a little bit of background on why we did this research, so you know what our product does. We have a vested interest in handling OS updates, app updates, security policy enforcement, and compliance for Apple devices. We have a high security bar for our products, so we've put a lot of work into ensuring it's secured by design. Our goal with this talk is to increase the security of MDM and DEP, and also raise the bar for all MDM vendors. Plus, I just wanted to work with Jesse again. Let's quickly go through the agenda. We'll cover some basics, terminology, and concepts, followed by an overview. Then, we'll dive deep into the topic, with Max guiding us. We'll also disclose the vulnerability we found and explain how it works. After that, we'll actually exploit the vulnerability, and if all goes well, our demo will work without any issues. Finally, we'll discuss the fix, provide some conclusions, and share takeaways. Let's jump in! So, what is MDM? It can be a confusing term because it refers to an entire product category. When we say MDM, we specifically mean Apple's flavor of MDM, which is a protocol. It also includes a few other things that we'll touch on. The purpose is to set system configurations in a centralized way through an MDM server. This server is built by a third party, not run by Apple. It could be Fleet Smith or another product like AirWatch. Mobile device management products fall under this category. An MDM server can...
Award-winning PDF software





Video instructions and help with filling out and completing Dd 1750